Skygofree Real Download For Android
The Skygofree spyware analyzed by Kaspersky today was first spotted by the researcher Lukas Stefanko and the first analysis was published last year by the experts of CSE Cybsec ZLab.
Skygofree (one of the most powerful strains of Android spyware) has been discovered. Security researchers from Kaspersky have found one of the most powerful strains of Android spyware that enable attackers to take full control over the infected devices remotely. The Russian antivirus provider concluded the software, which it dubbed Skygofree, was one of the most powerful seen aimed at Android operating systems,” wrote Thomas-Fox. “The surveillance tool was being delivered via a handful of websites, including fake network update pages from different telecoms giants, including Three and Vodafone, all.
- Download My Talking Tom 6.2.0.910 for Android for free, without any viruses, from Uptodown. Try the latest version of My Talking Tom 2020 for Android.
- The 0.12.0 PUBG Mobile latest upgrade arrives today. The latest PUBG Mobile 0.12 upgrade is about to come out fresh out of the oven. After their incredibly successful collaboration with Capcom Resident Evil 2, which was released this past month February, the survival modes have been strengthened and other related game modes have been added as a way to help you face the unending mobs of zombies.
- For example, the latest version of Android can automatically stop inactive processes to save battery power, but Skygofree is able to bypass this by periodically sending system notifications. And on smartphones made by one of the tech majors, where all apps except for favorites are stopped when the screen is turned off, Skygofree adds itself.
- Android threat-of-the-year so far in 2018, at least if you measure by media interest, is the curiously-named SkyGoFree malware. (The name was apparently invented by researchers at Kaspersky.
A few days ago, malware researchers at Kaspersky Lab had disclosed the discovery of a new strain of mobile malware; it is powerful Android spyware dubbed Skygofree.

Skygofree is Android spyware that could be used to gain full control of infected devices remotely, the features it implements make this threat very useful in targeted attacks.
The analysis conducted by Kaspersky revealed that Skygofree was used against many users for the past four years, most of them in Italy.
It is important to clarify that the name Skygofree is not linked to Sky Go, which is the subsidiary of Sky and does not affect its services.
The malware has been in the wild at least since 2014, and it was improved several times over the years.
“At the beginning of October 2017, we discovered new Android spyware with several features previously unseen in the wild. In the course of further research, we found a number of related samples that point to a long-term development process. We believe the initial versions of this malware were created at least three years ago – at the end of 2014,” reads the analysis published by Kaspersky.
“Since then, the implant’s functionality has been improving and remarkable new features implemented, such as the ability to record audio surroundings via the microphone when an infected device is in a specified location; the stealing of WhatsApp messages via Accessibility Services; and the ability to connect an infected device to Wi-Fi networks controlled by cybercriminals.”
Is this the first time that malware researchers have discovered this threat?
The answer is negative, the malware was first observed by the security researcher at ESET Lukas Stefanko, and a first detailed analysis of the Skygofree spyware was published by the experts at the CSE Cybsec ZLab.
The researchers at the ZLab published in November a report titled “Malware Analysis Report: Fake 3MobileUpdater” after obtained a sample of the malware, immediately emerged that the malicious code was developed for surveillance purposes by an Italian firm, likely operating for law enforcement.
According to Kaspersky, Skygofree has being distributed through fake web pages mimicking leading mobile network operators. The analysis of the domains used in the attack revealed they were registered since 2015.
The most recently observed domain was registered on October 31, 2017, according to Kaspersky telemetry data, the malicious code was used against several individuals, the victims were exclusively in Italy.
The team of researchers at CSE CybSec ZLab analyzed in November a fake 3 Mobile Updater that was used pose itself as a legitimate application of the Italian Telco company, TRE Italia.
“The most classic and efficient method used to lure the users is to believe that the application does something good. This is just what 3 Mobile Updater does. In fact, this malicious Android application looks like a legitimate app used to retrieve mobile system update, and it improperly uses the logo of the notorious Italian Telco company, TRE Italia, in order to trick victims into trusting it,” reads the report published by CSE CybSec.
Figure 1 – 3 Mobile Updater analyzed by CSECybsec in 2016
The analysis conducted by Kaspersky suggests the involvement of an Italian firm due to the presence in the code of strings in Italian.
“As can be seen from the comparison, there are similar strings and also a unique comment in Italian, so it looks like the attackers created this exploit payload based on android-rooting-tools project source code,” states Kaspersky.
The CSE CybSec researchers shared the same conclusion, below a portion of the code analyzed by the members of the ZLab.
“Moreover, both in the logcat messages and in the code, the malware writers used the Italian language. So, we can say with high confidence that this malicious app has been written by an Italian firm that intended to target users of the Italian telco company Tre,” CSE wrote in the analysis.
The artifacts analyzed by Kaspersky in the malware code and information gathered on the control infrastructure suggest the developer of the Skygofree malware is an Italian IT company that works for surveillance solutions.
Kaspersky Lab has not confirmed the name of the Italian company behind this spyware, we at the CSE CybSec ZLab opted for the same decision in October due to the possible involvement of law enforcement or intelligence Agencies.
Unfortunately, the OPsec implemented by the firm is very poor. The name of the company is present in multiple references to the code, and the domains used as C&C servers were registered by the Italian tech firm.
“Although the security firm has not confirmed the name of the Italian company behind this spyware, it found multiple references to Rome-based technology company ‘Negg’ in the spyware’s code. Negg is also specialized in developing and trading legal hacking tools,” states the blog post published by THN.
Once installed, Skygofree hides its icon and starts background services to conceal its malicious actions from the victim, one interesting feature implemented by the malicious code prevents its services from being killed.
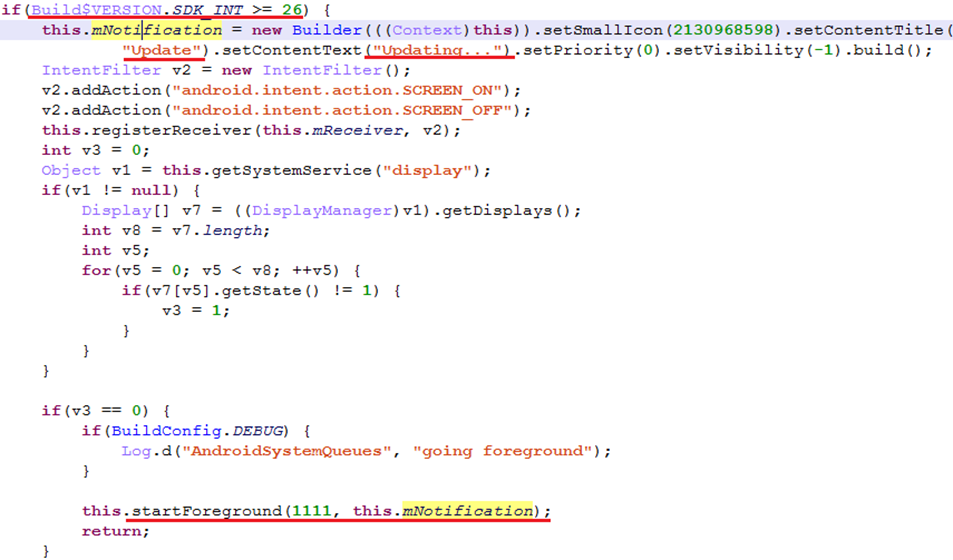
“Interestingly, a self-protection feature was implemented in almost every service. Since in Android 8.0 (SDK API 26) the system is able to kill idle services, this code raises a fake update notification to prevent it,” continues Kaspersky.
Kaspersky published an interesting analysis of the Skygofree spyware, according to the firm the malicious code was enhanced since October implementing a sophisticated multi-stage attack and using a reverse shell payload.
Skygofree Real Download For Android Phones
The malicious code includes multiple exploits to escalate privileges for root access used by attackers to execute sophisticated payloads, including a shellcode used to spy on popular applications such as Facebook, WhatsApp, Line, and Viber.
The same spying abilities were implemented in the app analyzed at the CSE CybSec.
“The capabilities of this malicious app are enormous and include the information gathering from various sources, including
the most popular social apps, including Whatsapp, Telegram, Skype, Instagram, Snapchat. It is able to steal a picture from the gallery, SMS and calls registry apps. All this data is first stored in a local database, created by the malicious app, and later it is sent to the C2C,” reads the preliminary analysis published on SecurityAffairs.
“There are multiple, exceptional capabilities: usage of multiple exploits for gaining root privileges, a complex payload structure, [and] never-before-seen surveillance features,” the researchers said.
Skygofree implements the main surveillance features; it can take pictures and videos remotely, monitor SMSs, call records and calendar events, of course, it also able to gather target’ location and access any information stored on the mobile.
Skygofree also can record audio via the microphone, an interesting feature implemented by the spyware allows the attacker to force the victim’s device to connect to compromised Wi-Fi networks it controls to conduct man-in-the-middle attacks.
Kaspersky also found a variant of Skygofree targeting Windows users, a circumstance that suggests the Italian firm is also targeting machines running Windows OS.
The best way to prevent yourself from being a victim is to avoid downloading apps via third-party websites, app stores or links provided in SMS messages or emails.
The journalist Thomas-Fox from Forbes magazine wrote an interesting article about Skygofree some hours after the publishing of the Kaspersky report. Thomas searched for archived versions of the website used by the Italian firm Negg and discovered that the company was looking for software engineers with experience in Android and iOS development.
It was requested to the candidates the “knowledge of the techniques of dynamic and static analysis of malware.”
“That chimed with the Kaspersky research, which found only a few infections, all within Italy. The Russian antivirus provider concluded the software, which it dubbed Skygofree, was one of the most powerful seen aimed at Android operating systems,” wrote Thomas-Fox.
“The surveillance tool was being delivered via a handful of websites, including fake network update pages from different telecoms giants, including Three and Vodafone, all registered in 2015. “
I asked my colleague Dr. Antonio Pirozzi, Director of the CSE CybSec ZLab, to compare the stubs of code shared by Kaspersky with the ones related to the code we analyzed back in November.
This is what has emerged from the comparison.
- These classes are identical:
Skygofree Real Download For Android Tv
- The spyware CSE Cybsec analyzed did not contain the Android exploits found by Kaspersky, as well as the reverse shell PRISM and the busy box.
- However, also the class used for parsing are similar;
Moreover, the DNS used are the same;
The analysis published by Kaspersky included Indicators of Compromise, including the URL of the C&C (url[.] plus) which was the same of the Spyware analyzed by CSE CybSec.
“Definitely we have a lot of evidences inside the spy tool that link the threat to the Italian firm. The Italian company’s name is everywhere in the code, and the whois records of the C&C are registered by the same firm. This lets me think that someone was protecting these hackers. We are uncovering a Pandora Vase,” added Dr. Antonio Pirozzi.
Many parts of the code are identical; both source code includes strings in Italian and the reference to the Italian firm are the same. The version analyzed by Kaspersky is a new release of the malware first analyzed by CSE CybSec ZLab.
Kaspersky also shared the URL from which the spyware is downloaded, and one of them was related to the version we analyzed (Fake 3 mobile updater).
The two version of the malware shared numerous classes, C&C server, Whois records and many other info. The sample analyzed by CSE was probably still under development.
The discovery of the tool and the simplicity in attributing it to a specific actor is disconcerting and raises serious questions about the way surveillance activity must be conducted. For an intelligence agency was not complicated to identify the surveillance activity conducted using software like Skygofree and variously interfere with the operation.
Android threat-of-the-year so far in 2018, at least if you measure by media interest, is the curiously-named SkyGoFree malware.
(The name was apparently invented by researchers at Kaspersky, simply because they “found the word in one of the domains” used in one of the samples they looked at – the malware isn’t targeted at users of the telecommunications company Sky or its Sky Go TV product.)
In one word, SkyGoFree (or SkyFree as Sophos products detect it) is easily described: spyware.
A quick look in the decompiled Java code of the malware reveals the range of data it knows how to steal:
RUBRICA, in case you are wondering, is Italian for ADDRESS BOOK. A lot of the code seems to have been written by Italian speakers – the lines above come from a source file called Costanti.java, which would be Constants.java in English.
There’s loads more treacherous functionality in the malware, including a function called StartReverse() that connects your phone up to a server run by the crooks to given them what’s called a reverse shell.
Skygofree Real Download For Android Phone
Normally, to logon into a command prompt (known in Unix and Linux as a shell) you need to initiate a connection to a device, which means getting through any firewalls and network address translation that’s in the way.
Many mobile networks, and almost all Wi-Fi networks, let you make outbound connections to other people, but don’t let others connect inbound directly to you – you’re supposed to be a data consumer (client) on the the network, not a data producer (server). Download sabrina movie harrison ford.
Hackers get around this with a reverse shell: a common intrusion trick that turns the logon process on its head.
Your device initiates the connection outwards to the crooks, but only to set the connection up; after that, your device acts as the server, with the crooks hooked up as clients, “logged in” with direct control over your phone.
SkyGoFree also includes a feature – if that is the right word – that it calls Social to let the crooks grab data from numerous other apps on your device.
Here’s an edited fragment of the code that tries to steal your social networking data (don’t worry if you don’t understand Java – this is just by way of illustration):
The good news is that on a regular Android phone, apps can’t blindly read each other’s data.
Unless you have rooted your device, or have an old or unpatched phone with a security hole that allows malware to root your phone automatically and secretly in the background, this part of the malware won’t work.
SkyGoFree also has a component that can call home to download and install additional modules – a sort-of plugin system for the malware. (When we investigated, the addon files that the malware was looking for were offline.)
Malware is often programmed so that it can update or extend itself, which makes the threat even more serious: neither you, nor researchers, can ever be sure in advance exactly what the crooks might decide to do with infected devices in the future.
What to look for
Skygofree Real Download For Android Download
The sample we examined pretends to be a “System Update”, using a green Android icon:
If you launch the app, it starts running in the background but almost immediately removes its own icon to give you the impression that the “update” has finished.
Fortunately, the app still shows up on the SystemApps page, where you can stop it and uninstall it:
We haven’t received any reports of this malware from the wild, and it isn’t – and as far as we know, never was – in Google Play, so you’d have to go to the SettingsSecurity page and turn on the non-default option to Allow installation of apps from unknown sources to get infected:
Google Play is not the virus-free walled garden that you might have been led to believe, but it is still far safer than accepting apps from unknown sources such as alternative markets, unregulated Android forums or links sent to you by friends.
What to do?
- Stick to Google Play. If you need to go off-market for a specific app, go back into
SettingsSecurityafter installing it and turnAllow unknown sourcesoff again. - Use an Android anti-virus. Products like the free Sophos Mobile Security for Android will help you block malware and warn you about insecure settings on your device.
- Don’t trust system updates offered by third parties. Be especially cautious of “updates” that claim to offer additional features or services not available officially.